Beware of max_input_vars php ini configuration option
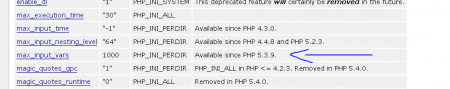
If you are updating PHP on your production server, beware of relatively new max_input_vars php.ini directive which is now 1000 by default. That means if you have 1001 form field – only 1000 form fields will be submitted. Use of this directive mitigates the possibility of denial of service attacks which use hash collisions in connection with CVE-2011-4885.
From php changelog:
2012-01-03 : security / trunk - Added php-5.2-max-input-vars patch max_input_vars directive to prevent attacks based on hash collisions - CVE-2011-4885
Why we have so much form fields is a subject for different post. The main problem is that even php site says this update is available from PHP version 5.3.9. The fact is we have 5.3.2-1ubuntu4.14 and the update is there.
So… you know… beware. :)

3 thoughts on “Beware of max_input_vars php ini configuration option”
July 11, 2012 at 15:57
Same problem with PHP PHP 5.1.6 (!) on prroduktiv Redhat ES Server
July 26, 2012 at 23:50
Thank you for posting that…by the way we had problems with this directive using version
5.3.2-1ubuntu4.15.
January 12, 2014 at 14:45
To help warn people of this problem, I have created a plugin for WordPress:
http://wordpress.org/plugins/wp-max-submit-protect/
This plugin will monitor, at the front end, how many fields a form is about to post. If it exceeds the server limit, then it will warn you and give you a chance to cancel the submit, fix your server settings, then try submitting again. Hope you find it useful.